Distributed denial of service protection
Ensure availability and performance with RedShield’s advanced DDoS protection. Keeping you online, and secure – so you can get on with business.
DDoS protection comes as standard with every shielding plan. We work with specialist global providers to ensure your apps remain resilient.
Key benefits
- Working through AWS, we have an ultra high capacity network (Scrubbing capacity up to 110 Tbps)
- Protect against volumetric, protocol, application layer attacks
- Optional DDoS simulation testing
- Expert assistance and 24 x 7 support
- No per-attack fees, attack volume or usage limits
Our global providers
With attacks growing in size and complexity, we work with an ecosystem of specialist global providers to ensure our customers remain secure and available.


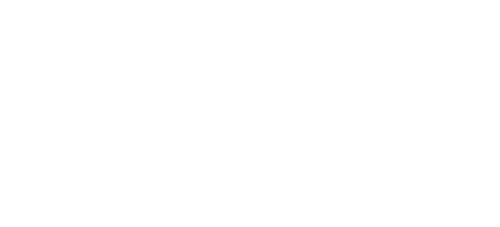
Minimizing risk, maximizing uptime
We know how critical it is to keep your web apps online. RedShield’s globally distributed edge network provides an advanced layered defence against volumetric, protocol and sophisticated layer 7 (application level) DDoS attacks.
Through this we are able to effectively morph our defences continuously based on new attacks coming in and we deliver application availability and security as a measurable outcome to you.
Ensuring your applications are resilient, hardened, and cloud-ready
For your applications to keep serving legitimate incoming requests in the face of an attack, you need advanced defenses.
RedShield’s automated system is able to distinguish good and bad traffic by throwing an array of escalating challenges. For example, our system utilises databases, identifies browser plugins, employs the use of heuristics and can serve CAPTCHA’s all to determine whether or not the request is a bad actor.
We’ll keep the attacks at bay, while you let your customers continue to play.
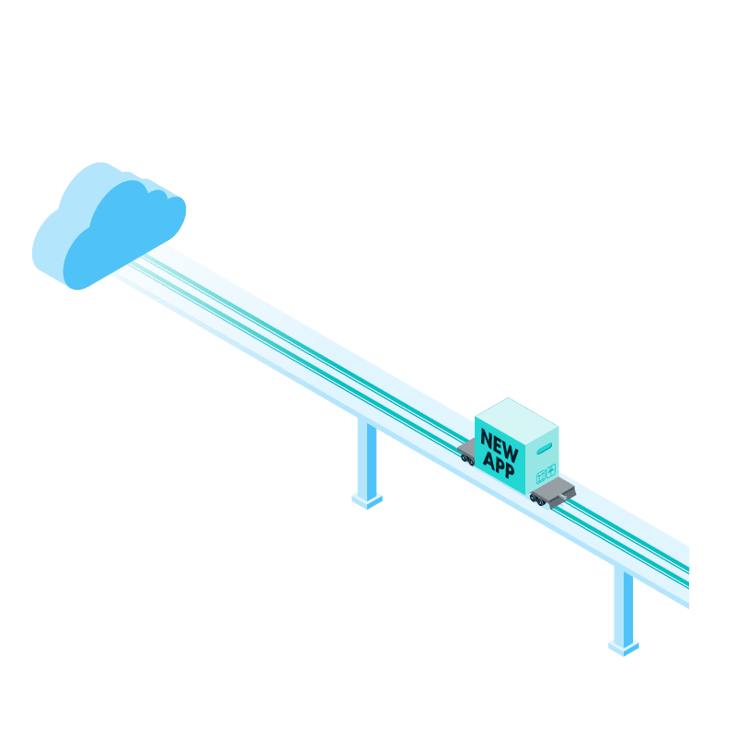
Helping you get DDoS-ready
- Simulating current DDoS attack types and trends in a controlled environment
- Fire-drilling your incident response
- Delivering a report identifying strengths and weaknesses, and detailing clear steps to improve resiliency
- Working with your team to tailor controls to your environment, with thresholds for alerting and rate limiting based on your system capacity
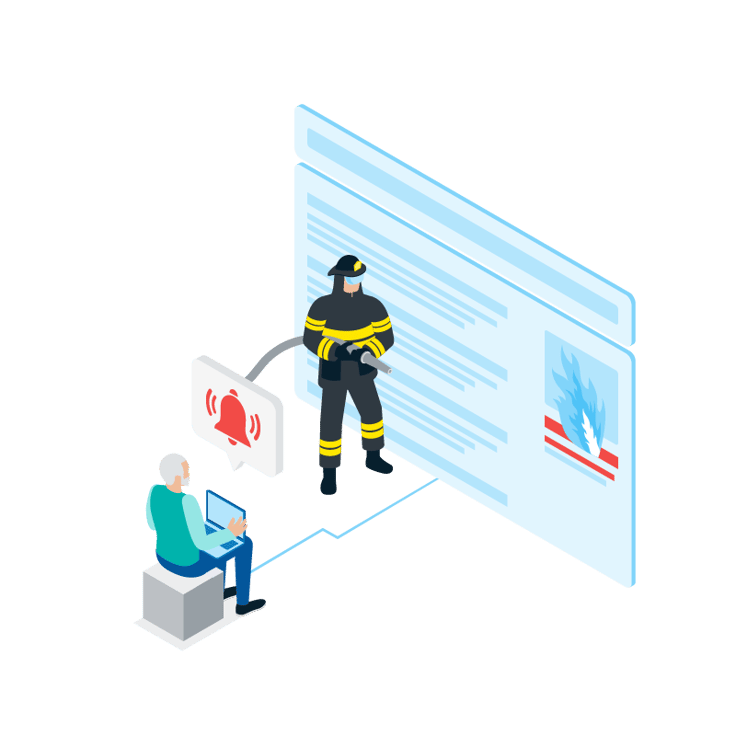
Always on-alert
Our team of battle-hardened security professionals live on the front line, so responding to and successfully mitigating a significant layer 7 denial of service (DoS) attack is just another day in the office. In the case of an incident, our team acts as an extension of yours to keep your customers happy and avoid disruption to business operations.
DDoS protection comes as standard with every shielding plan
RedShield shields your application and API vulnerabilities from attack, so you can get on with business.
Shields are small blocks of code designed to fix an otherwise exploitable vulnerability in an application. We can get shields up and running in hours, with no integration required, no impact on legitimate application functionality, and without touching your code.
Integrating with your change management, incident management, and operational reporting procedures, RedShield’s AI-powered, expert-managed solution becomes an extension of your cybersecurity operation.
“The journey with RedShield has been excellent. Everyone we’ve engaged with is very knowledgeable, and they are extremely responsive. It’s what we needed to help navigate the ever-changing digital landscape”
- Patrick Wake, Head of Information Security at FDM Group
"RedShield's DDoS controls, expertise and network scrubbing capacity helped to ward off an attack that targeted at us. The team know what they are doing and have a world class system to manage things in a crisis, which gives me confidence"
- CISO, Telecommunications Industry
Related articles
Strengthening DNS Security: A Case Study in Cybersecurity Excellence
This article explores a real-world scenario where RedShield demonstrated its expertise in defending a high profile NZ government agency against a DDoS attack.
View content
Enhancing Cyber Resilience through Proactive Measures and Advanced AWS...
This article explores a real-world scenario where RedShield demonstrated its expertise in defending a high profile NZ government agency against a DDoS attack.
View content
Case Study
Securing a Third-Party App That Can’t Be Touched
Find out how a government agency secured an application built by a third party developer that could no longer be found.
View content


